Abstract: The elements that comprise a network that facilitates the development of improvised explosive devices (IED) are not dissimilar from the elements that lead to the proliferation of weapons of mass destruction (WMD). IED employment has burgeoned in recent years, with over 16,000 incidents worldwide in a 12-month period, while there have been over 500 WMD incidents by non-state actors in the last 26 years. The possibility of the profit-minded suppliers within vast, transnational IED networks expanding into WMD proliferation is high due to the opportunity for profits at relatively low additional risk. The convergence of these two seemingly separate networks does not mean that an IED facilitation network will suddenly market WMD, rather that non-state actors could employ these networks to gather the knowledge, people, materials, finances, and infrastructure required for WMD development and employment. This potential convergence of IED facilitation networks and WMD proliferation networks should be better understood in order to prevent greater proliferation of WMD.
During the 12-month period between September 1, 2017, and August 31, 2018, there were “approximately 16,300 reported” improvised explosive device (IED) incidents worldwide, not including those within the United States.1 These attacks caused over 25,000 casualties. Of these incidents, roughly 37 percent (approximately 6,000) occurred outside of Iraq and Afghanistan in countries like Nepal, Colombia, and India. The number of incidents worldwide highlights the growth of IED facilitation networks by—as John Caves, Deputy Director of the Center for the Study of Weapons of Mass Destruction at National Defense University, put it—“profit-minded suppliers” to meet the demand.2 Similarly, there has been a growth in the number of weapons of mass destruction (WMD) incidents by non-state actors.a According to the Global Terrorism Database (GTD), between 1990 and 2016, there were 525 such events—of which 400 were chemical, 107 were biological, and 18 were nuclear.3 b Between 2013 and 2016, the last year for which such information is available via GTD, the planned use or actual use of a chemical, biological, or nuclear device was on the rise.c
The increasing rate of WMD incidents associated with non-state actors demonstrates their desire to possess a WMD, whether developed internally or acquired externally. IED facilitation networks, however, have been far more successful in disseminating the knowledge, technology, and material required to manufacture and employ an IED worldwide. There is growing concern among counterproliferation practitioners and policy makers that an IED facilitation network with an already existing, diversified, and far-reaching structure could converge with a WMD proliferation network, leading to wider dissemination of WMD to non-state actors—that is, the merging of “terrorists with profit-minded suppliers exploiting the opportunities created by globalization.”4 Convergence between IED facilitation and WMD proliferation networks could potentially lower existing thresholds, making proliferation of WMD not only easier but more widespread.
Background
In the context of discussing threats, former European Command Commander Admiral James G. Stavridis defined convergence as “the merger of a wide variety of mobile human activities, each of which is individually dangerous and whose sum represents a far greater threat.”5 The concept of network convergence relates to one network crossing over and enhancing the capabilities of another, instead of contributing a specific technology. For example, the international human smuggling networks that typically smuggle criminals, fugitives, terrorists, trafficking victims, and migrants overlap and link with drug trafficking networks in certain areas.6
The United States, spearheaded through the Department of Defense in conjunction with other agencies, has sought to counter IED facilitation networks to prevent their presence on the battlefields of Iraq and Afghanistan. The organization dedicated to this mission is the Joint Improvised-Threat Defeat Organization (JIDO), formally known as Joint Improvised Explosive Device Defeat Organization (JIEDDO), which is a component of the Defense Threat Reduction Agency. In 2013, then JIEDDO Director Lieutenant General Michael Barbero, during a seminar at Johns Hopkins University, highlighted that IED facilitation networks are transnational, composed of human capital—ranging from financiers, smugglers, training camps, technical experts, and propagandists—and utilize readily available material and dual-use technology.7
IED Networks
Improvised explosive device proliferation can occur, simplistically speaking, in two ways. The first is through consolidated proliferation, where the process is centralized such that IEDs are manufactured internally and then dispersed for employment. The second method of proliferation is disparate. Raw components and knowledge are disseminated to the tactical/employment level where IEDs are manufactured and deployed. The first method enables leadership to maintain control of the process and knowledge required for manufacturing, while the second relinquishes control and knowledge down to numerous semi-independent subgroups.
From the vantage point of terrorists, both means of proliferation have their advantages and disadvantages, and regardless of the method, both require the same components, which are dual-use in nature and transported internationally on a daily basis. The components of an IED are relatively basic: an explosive main charge, initiating system, and casing. Frequently, particularly with non-state actors, the main charge consists of a homemade explosive, typically derived from ammonium nitrate fertilizers. Companies legally ship tons of fertilizer all over the world to assist farmers in both developing and developed countries. Ammonium nitrate fertilizers themselves are harmless but can be easily modified into an explosive. A Conflict Armament Research report found that Islamic State forces, or intermediaries acting on their behalf, acquired IED components including “chemical precursors such as fertilizer, containers, detonating cord, cables, and wires … manufactured or sold in Turkey” and transferred them to Iraq.8 Within the United States, Timothy McVeigh acquired the same type of materials domestically to bomb the Murrah Federal Building in Oklahoma City in 1995.
The initiating system of an IED has a few subcomponents, including a power source, switch, and initiator, which can be a simple safety fuse or piece of explosive cord. The initiation system receives an electronic signal and then uses the power supply to trigger the initiator, which propagates the signal into the main charge. The casing is simply the outer elements that hold the main charge and initiation system together. The shape and material of the casing can assist in directing the explosive force of the detonation.
All the elements of an IED are dual-use components and can be acquired virtually anywhere in the world. Although the knowledge required to modify these precursors and materials into a device is not common, it does not require an advanced degree in chemistry or physics. Indeed, organizations such as al-Qa`ida and the Islamic State have propagated this knowledge to their followers around the world via the internet and hands-on training.9
WMD Networks
An article by Amy Frumin, Tracy Moss, and David Ellis published in National Defense University’s PRISM deconstructs WMD proliferation networks into their basic components.10 d (See Figure 1 for a visualization of this deconstruction.) Networks are composed of people, material, infrastructure, money/finance, information, and lines of communications, which can be both physical and virtual. As highlighted in the PRISM article, ‘people’ can refer to scientists, brokers, workers, and engineers in the network. ‘Material’ can range from parts and raw materials to weapons, tools, and chemicals. ‘Infrastructure’ can be either physical (lab or reprocessing facility) or virtual (cyber). Money is simply the financial resources required to develop the WMD. Information is the data, knowledge, orders, and facts. Lines of communications can be both physical and virtual, and pertain to the movement of information, money, and material.11 Depending on the terrorist organization and potential support from a state sponsor, WMD proliferation can occur either under central leadership or through informal and disperse relationships.
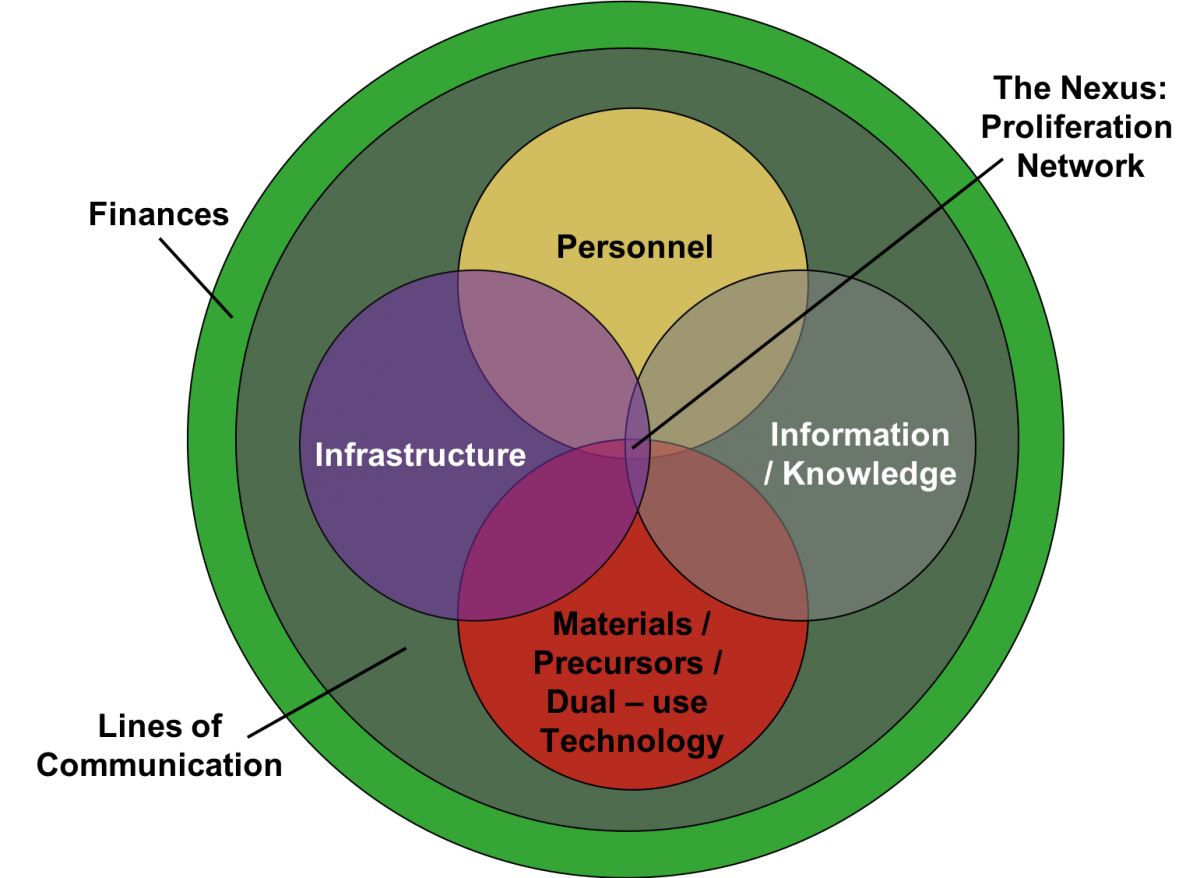
While the threshold for IED proliferation in terms of knowledge, materials, and skill is low, the WMD proliferation threshold by non-state actors has been relatively high. The type of WMD and desired method of employment contribute to the proliferation threshold. As previously mentioned, there have been 525 WMD incidents by non-state actors in a 26-year period, to include recent incidents with chemical weapons by the Islamic State and individuals within the United States who possessed the toxin ricin. In examining the network requirements outlined by Frumin, Moss, and Ellis, it is possible to deduce that WMD proliferation is heavily dependent on several factors such as knowledge, skilled personnel, infrastructure, and dual-use technology, with the exact dependence dictated by the type of WMD to be developed.
Perhaps the most notable WMD proliferation network was Abdul Qadeer Khan’s nuclear technology network. Through a series of unconnected real and fake companies around the world, forged end-user certificates, unwitting shipping companies, and ignorant customs officials, A.Q. Khan was able to sell weapon designs, centrifuges, and raw materials to multiple states including Iran, Libya, and North Korea. As David Albright, Paul Brannan, and Andrea Stricker have highlighted, “the A.Q. Khan network demonstrated that it is possible for a shady transnational network of engineers, industrialists, and businessmen to sell turn-key nuclear weapons production facilities … The conditions that led to the network remain: buyers with cash and people with access to classified nuclear know-how experience at designing as well as building nuclear facilities, and trafficking skills.”12 While A.Q. Khan’s network sold materials to state actors, he could have just as easily sold the material to non-state actors. This does not imply that a terrorist could easily develop and employ a nuclear weapon, but rather that there are profit-minded suppliers willing to sell components to them.
While Molly MacCalman states “the link between trans-national illicit networks and nuclear proliferation thus remains central since most countries, and certainly most terrorist organizations, will depend for the foreseeable future on illicit trade for the acquisition of nuclear equipment, material, and expertise,” the dependence on these networks holds true for both chemical and biological weapons development as well.13 Turkish Member of Parliament Eren Edrem, for example, claimed that chemical precursors necessary for the Islamic State to make sarin were smuggled through Turkey.14 While there is no evidence that the Islamic State ever made the nerve agent sarin, findings by the organization Conflict Armament Research showed that the Turkish domestic market plays a predominant role in supplying chemical precursors for homemade explosives (HME).15 While these precursors tend to be used for manufacturing homemade explosives, there is little difference between some HME precursors and a chemical weapon agent precursor. Similar to the vast majority of international shipments that occur daily, there is nothing illegal about shipping these raw materials themselves, especially since they have a dual-use in legal industries. It is the potential trans-loading, redirection, and end use of these proliferation components that result in the illegal development of chemical, biological, and possibly nuclear weapons.
In another example, there have been several ricin incidents in Western countries, including the United States and Germany, in the past few years—for example, several letters containing the toxin sent to U.S. government officials in October 2018.16 Ricin is a simple toxin that can be extracted from castor beans and requires little knowledge to create but great skill to weaponize effectively, along with a few critical materials. The extraction is not the most complex process—one that a biochemist or molecular biologist might do on a daily basis, for example—but for the untrained, it can prove difficult. There is nothing illegal about possessing castor beans, possessing the knowledge of protein extraction and purification, or possessing equipment required to complete the process, but it is rare that a single individual or group would have all three readily available. The non-state actor generally requires a network to provide these materials and capabilities, regardless of whether the network is actively conspiring with the actor (illicit networks) or an unwitting accomplice (licit networks).
As highlighted in Figure 2, the pathway to WMD proliferation, like that of IED proliferation, is not linear. It is rare that a single individual would have the financial means and access to knowledge, materials, and infrastructure to single-handedly proliferate IEDs, let alone WMD. The Islamic State, for example, had only 109 (2.7%) members with any sort of STEMe background listed in 4,100 captured personnel records, and yet it was able to develop and employ sulfur mustard agent in several locations.17 There are many factors and obstacles that must be overcome in order to move from concept and design to an employable weapon. Each step in the process can be seen as a discrete opportunity for interdiction. The path for employment is further complicated by the type of IED or WMD. Some simple IEDs merely repurpose artillery shells while others, such as the explosively formed projectile, require precise molding of a copper cap in order for it to transform into a molten slug capable of penetrating armor.
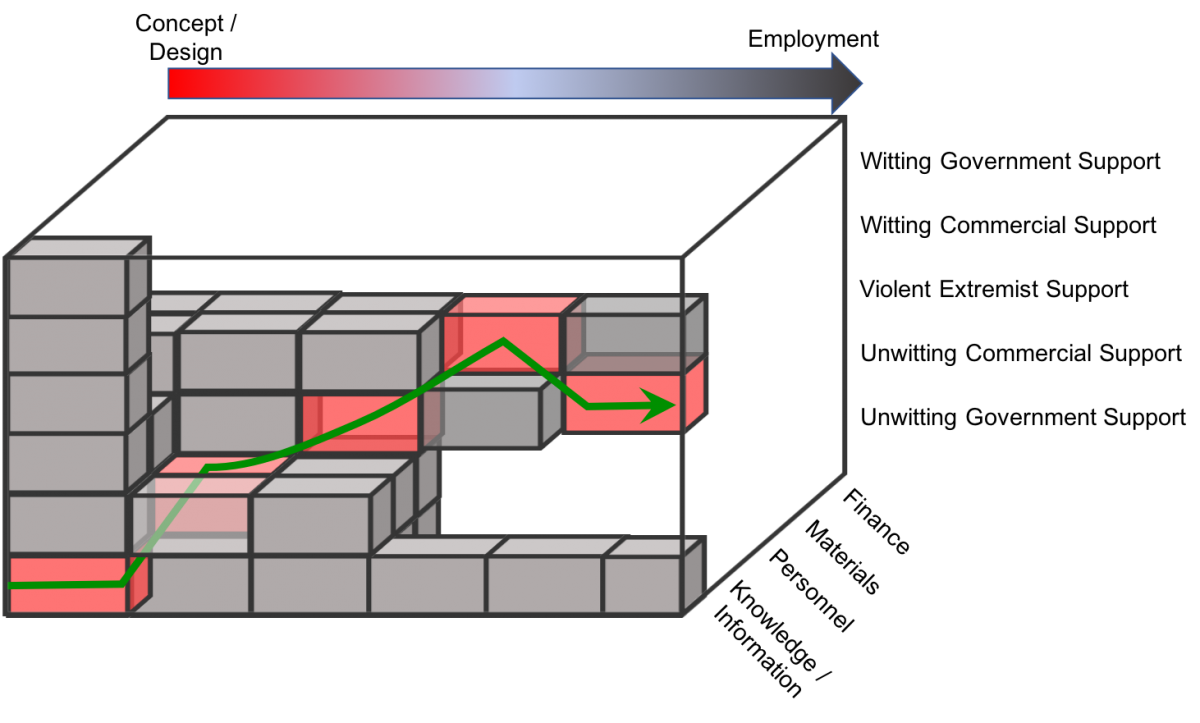
The complexity of the designed weapon dictates the intricacy of the proliferation network. The necessity for secrecy, resulting from U.N. Security Council Resolution 1540,f the nuclear non-proliferation treaty, the bioweapons convention, and the chemical weapons convention, also makes the proliferation pathways more convoluted.
Conclusion
Despite the different end-states of these two networks, IED or WMD, the elements of each are similar. It is this similarity that poses the risk and potential ease for an IED facilitation network to converge with a WMD proliferation network.18 If such convergence happens, in an effort to push materials, information, financial support, personnel, and equipment more quickly and efficiently, WMD proliferation to and among non-state actors will be considerably easier. To be clear, convergence does not relate to a specific piece of knowledge, material, or person, but rather describes the occurrence of one network crossing over and enhancing the capabilities of another network, such as the proliferation materials capable of WMD production. In this instance, profit-minded IED facilitators could easily begin pushing WMD proliferation components. While the taboo associated with WMD may deter some suppliers, others are likely to remain focused on the profits, especially since the increased risk can correspond to increased profits. This may be too tempting for some suppliers to resist.
Given the potential threats discussed in this article, there are strong arguments for expanding ongoing efforts that address IED facilitation networks, including applying lessons learned, to anticipate the potential for these same networks to proliferate the knowledge, material, financing, and access to infrastructure required for WMD development and employment. CTC
Major Stephen Hummel serves as Deputy, Commander’s Initiative Group (CIG) at the 20th CBRNE Command. Previously, he served in both Iraq and Afghanistan and as a USAREUR CBRN Plans Officer, an Assistant Professor in the Department of Chemistry and Life Science at the United States Military Academy, and a Nuclear Operations Officer on a Nuclear Disablement Team. He holds a B.A. in Political Science from Boston College, an M.S. in Free Radical and Radiation Biology from the University of Iowa, and an M.S. in Chemical and Physical Biology from Vanderbilt University.
Colonel F. John Burpo is the Department Head of Chemistry and Life Science at West Point. COL Burpo commissioned as an artillery officer and served in airborne, armor, and Stryker units with humanitarian, peace-keeping, and combat operational deployments. He also served as the Deputy Commander-Transformation for the 20th Chemical, Biological, Radiological, Nuclear, and Explosives Command (CBRNE). He earned a B.S. in aerospace engineering from West Point, an M.S. in Chemical Engineering from Stanford University, and Sc.D. in Bioengineering from the Massachusetts Institute of Technology.
Brigadier General James Bonner is the Commanding General of the U.S. Army’s 20th CBRNE Command in Aberdeen Proving Ground, MD. Previously, he was the 29th Chief of Chemical and CBRN School Commandant. Other key assignments include Plans and Policy Officer J-5 and as a Counterproliferation Planner J-3, Joint Special Operations Command (JSOC); and Special Assistant for Countering WMD Terrorism, Counterterrorism Division, Federal Bureau of Investigation (FBI). He holds master’s degrees from Central Michigan University and the Naval War College.
This article and overall project are supported by the Defense Threat Reduction Agency’s Project on Advanced Systems and Concepts for Countering WMD (PASCC) and administered through the United States Air Force Academy’s Institute for National Security Studies. The views expressed in this article are solely those of the authors and do not reflect the policies or perspectives of the United States Government, Department of Defense, the United States Military Academy, or the 20th CBRNE Command.
Substantive Notes
[a] Weapons of mass destruction are commonly characterized as nuclear, chemical, and biological, and can provide “states or sub-national groups the ability to inflict damage that is wholly disproportionate to their conventional military capabilities.” Even within the WMD realm, both destructive capability and the requirements to develop and employ the weapons differs greatly. Randall Forsberg, William Driscoll, Gregory Webb, and Jonathon Dean, Nonproliferation Primer: Preventing the Spread of Nuclear, Chemical, and Biological Weapons (Cambridge, MA: MIT Press, 1999).
[b] While no non-state actors were able to acquire a nuclear device, these 18 incidents represent distinct attempts where non-state actors were thwarted in acquiring significant quantities of special nuclear material, which are Uranium-235 and Plutonium-239. These two specific isotopes are the fissile material required to make a nuclear weapon.
[c] According to the Global Terrorism Database, there were 18 chemical, biological, or nuclear attacks in 2013, 24 in 2014, 29 in 2015, and 31 in 2016. Global Terrorism Database, National Consortium for the Study of Terrorism and Responses to Terrorism (START), University of Maryland.
[d] Within the Department of Defense (DoD), the counter-WMD role shifted between Combatant Commands in 2017 from U.S. Strategic Command to U.S. Special Operations Command, as highlighted in DoD Directive 2060-02.
[e] Science, technology, engineering, and mathematics.
[f] This U.N. Security Council Resolution from April 2004 states that “states shall refrain from providing any form of support to non-State actors that attempt to develop, acquire, manufacture, possess, transport, transfer or use nuclear, chemical or biological weapons and their means of delivery, in particular for terrorist purposes. The resolution requires all States to adopt and enforce appropriate laws to this effect as well as other effective measures to prevent the proliferation of these weapons and their means of delivery to non-State actors, in particular for terrorist purposes.” “UN Security Council Resolution 1540,” United Nations, April 28, 2004.
Citations
[1] “Global Improvised Threat Trends Update,” Joint Improvised Threat Defeat Organization, October 22, 2018.
[4] Caves.
[5] James Stavridis, “How terrorists can exploit globalization,” Washington Post, May 31, 2013.
[8] “Turkish Fertilisers Used in Islamic State IEDs in Iraq,” Conflict Armament Research, 2016.
[9] Daisy Muiba and Benjamin P. Nickels, “Foreign Technology or Local Expertise? Al Shabaab’s IED Capability,” CTC Sentinel 10:10 (2017); Iain Overton, Jacob Bernston, and Sue Eedle, “Understanding the Regional and Transnational Networks that Facilitate IED Use,” Action on Armed Violence, May 25, 2017.
[11] Ibid.
[15] “Weapons of the Islamic State,” Conflict Armament Research,December 2017, p. 98.
[16] “Islamic suspect detained in Germany tested ricin on hamster,” Reuters, August 3, 2018; Daniel Uria, “Navy Veteran Charged for Sending Toxin to White House, Pentagon,” UPI, October 18, 2018.
[17] Brian Dodwell, Daniel Milton, and Don Rassler, The Caliphate’s Global Workforce: An Inside Look at the Islamic State’s Foreign Fighter Paper Trail (West Point, NY: Combating Terrorism Center, 2016); Columb Strack, “The Evolution of the Islamic State’s Chemical Weapons Efforts,” CTC Sentinel 10:9 (2017).
[18] For a detailed discussion of the Islamic State chemical weapons threat, see Markus Binder, Jillian Quigley, and Herbert Tinsley, “Islamic State Chemical Weapons: A Case Contained by its Context?” CTC Sentinel 11:3 (2018).
 Skip to content
Skip to content

