Abstract: Following the U.S. drone strike that killed Iranian commander Qassem Soleimani, the U.S. government has issued repeated warnings to be vigilant against cyberattacks from Iran. In the immediate aftermath, Iranian social media disinformation operations, website defacements, phishing attempts, and network probing emanating from Iran spiked. Iranian hackers of all skill levels—from amateurs to professionals—appear to be taking the initiative to launch attacks they believe the regime would want them to undertake, whether or not they have received direct orders or requests from the government to launch these operations. Public reporting indicates that the Iranian regime itself has yet to retaliate for the commander’s death with a destructive cyberattack. Based on past behavior and the regime’s use of cyber as a tool in its asymmetric arsenal, it is likely that state-backed hackers will attempt to conduct significantly damaging cyber operations in the future. Soleimani’s death itself, however, is unlikely to significantly alter the trajectory of the cyber threat from Iran. State-sponsored Iranian cyber operations are likely to continue, either in direct response to Soleimani’s death, in reaction to U.S. economic pressure, or in pursuit of other regime interests.
Tensions between the United States and Iran have been escalating since the Trump administration came into office in January 20171 and withdrew from—and in November 2018 began reimposing sanctions lifted pursuant to—the 2015 nuclear agreement, formally known as the Joint Comprehensive Plan of Action (JCPOA).2 Washington has further escalated sanctions since then, and Iran has responded with violence and destabilizing activities across multiple domains.3 In total, U.S. sanctions have cost Iran $200 billion in investment and oil revenue, according to President Hassan Rouhani.4 Inflation is rampant,5 foreign exchange reserves are rapidly shrinking, and the country has entered a deep recession.6
In response, the regime and its Islamic Revolutionary Guard Corps (IRGC) have harassed and even bombed vessels traveling through the Persian Gulf,7 and downed a U.S. drone in international airspace.8 State-backed hackers have, among other things, increased targeted phishing attemptsa against private industry in the United States and around the world9 and against journalists and activists.10 Tehran also stands accused of launching drone and missile attacks on Saudi oil giant Saudi Aramco.b
While the Trump administration reportedly launched cyberattacks on Iran following the downing of the U.S. drone,11 the president ordered but then canceled military strikes minutes before their execution.12 After the Aramco attack, the Trump administration reportedly again used exclusively U.S. cyber tools, this time conducting an attack aimed at degrading Iran’s propaganda capabilities.13 As a result, the U.S. strike that killed General Qassem Soleimani, commander of the IRGC Quds Force, took the world by surprise.
The January 3, 2020, drone strike that killed Soleimani and Abu Mahdi al-Muhandis, commander of the Iranian-backed, U.S.-designated terrorist organization Kata’ib Hezbollah (KH),14 came in response to rocket attacks by KH that killed a U.S. contractor working on a military base in northern Iraq.15 The U.S. military first responded with airstrikes on KH targets in Iraq and Syria.16 Pro-Iranian protestors then attacked the U.S. embassy in Baghdad.17 A day later, the U.S. military launched its drone strike.
Commentators on both sides of the political spectrum fretted that the United States was on the “brink of war,”18 but the tensions that threatened to boil over have since returned to a simmer. Even as the Iranian regime responded to Soleimani’s killing by launching a barrage of missiles at U.S. military bases in Iraq, President Trump proclaimed that Iran “appears to be standing down.”19 Foreign Minister Javad Zarif similarly tweeted that the regime “concluded proportionate measures,” indicating that no further escalation was forthcoming.20
And yet, the threat that the Islamic Republic poses in cyberspace has not abated. Just as the regime is unlikely to cease its support for terrorism, pursuit of nuclear-capable intercontinental ballistic missiles, and aggressive behavior toward its neighbors,21 it is unlikely to cease its malicious cyber operations. Indeed, nearly three weeks after Soleimani’s death, the FBI urged businesses to remain on alert and review warnings about the conduct of pro-regime cyber operators.22
It is well understood that cyber can be an effective asymmetric tool for causing damage to more militarily powerful adversaries, particularly when deployed against the private sector. The U.S. intelligence community assesses that the Iranian regime is “capable of causing localized, temporary disruptive effects” and is constantly preparing cyberattacks against the United States and its allies.23 There is no indication that Soleimani’s death will fundamentally alter the regime’s regional ambitions or its modus operandi in the physical and cyber domains. Statements from both Iran’s Supreme Leader Ali Khamenei and from Soleimani’s successor, Esmail Qaani, have emphasized the continuity of Iranian policy despite the change of leadership.24
While Iran is generally considered a less sophisticated cyber actor than other U.S. adversaries, the regime and its hackers tend to be much less risk-averse.25 A common view held by researchers who follow the activity of Iranian hackers is that they are more likely to engage in destructive or disruptive attacks whereas their counterparts in other countries might be more inclined to quietly collect valuable data and intelligence.26 c
Kiersten Todt, the executive director of the Commission on Enhancing National Cybersecurity under President Barack Obama, explained, “Iran is dangerous because they have the intent, motivation and capabilities. While their cyber capabilities are not on par with Russia and China, they are innovative and can cause both physical and psychological disruption.”27
This article examines Iran’s cyber strategy, including by analyzing two significant operations in order to understand how the regime uses cyber as part of its asymmetric arsenal. The article then examines the malicious cyber activity emanating from Iran since Soleimani’s death and the overall cyber threat landscape with regard to Iran to begin to anticipate the type of state-backed, Iranian cyber operations that may occur in the short and medium term. This analysis leads to the conclusion that while the Iranian cyber threat is significant and persistent, Soleimani’s death may have little impact on the trajectory.
The Islamic Republic’s Cyber Strategy
Cyber operations are a key pillar of Iran’s strategy, which relies on asymmetric capabilities to battle its more powerful adversaries.28 Following the killing of Soleimani, retired Lieutenant General Vincent Stewart, former deputy commander at U.S. Cyber Command, testified before Congress that the regime views its cyber capabilities as a “vital tool of statecraft and internal security” and a “low cost” way to retaliate against its enemies.29
Like many nation states, Iran uses cyber operations to collect intelligence and conduct espionage, and like all authoritarian governments, the regime uses cyber to “silence and weaken” its internal opposition, according to a 2018 U.S. State Department report.30 In fact, most victims of regime cyber operations are Iranian citizens and expatriates, scholars Collin Anderson and Karim Sadjadpour have noted.31
When targeting the United States and its allies, the Iranian regime often directs its cyber operations against private industry, which is generally less well defended than U.S. government networks. As a result, Tehran is able to target the soft underbelly of its more powerful foes. These cyber-enabled economic warfare operations appear to be Iran’s attempts to warn its adversaries that just as the United States can cause economic damage to its enemies by using financial sanctions, Tehran can undermine the strategic capabilities of its enemies by targeting their economies with cyberattacks.32
Externally, Saudi Arabia has borne the brunt of Iranian malicious cyber operations in recent years. Even when Iranian operatives target numerous government and private entities over the course of a campaign, private cybersecurity firms consistently find that the plurality of victims are Saudi.33 This is likely because the two states are bitter regional rivals and because Saudi cyber defenses are weaker than those of Iran’s other primary foes, Israel and the United States.34 For example, after Israel’s Cyber Defense Directorate detected an Iranian attempt in 2017 to infiltrate and possibly corrupt its home front missile alert system, the division was able to quickly excise the hackers, assess what they had accessed, and reinforce network defenses.35
In contrast, despite suffering substantial losses when the Shamoon computer virus hit state-owned oil company Saudi Aramco in 2012 (discussed later), Riyadh’s systems were insufficiently reinforced such that four years later, hackers working on behalf of the Iranian regime were able to use a new variation of the virus to corrupt computers at more than a dozen Saudi government agencies and businesses.36
There are two other explanations related to the comparative weakness of Riyadh’s defenses that are worth mentioning. Iranian hackers may be practicing against an easier target to hone their skills before pivoting to attacking the United States or Israel. Or, these hackers may be attempting to attack the United States, Israel, and Saudi Arabia with the same frequency but because U.S. and Israeli defenses are stronger, these two nations are able to suppress threats quickly and quietly whereas attacks on Saudi Arabia are more likely to be reported.
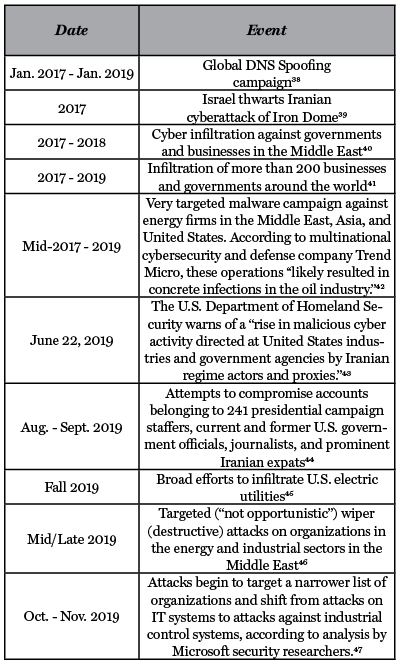
To understand how cyber capabilities fit into Tehran’s asymmetric toolbox, it is worth examining two of the regime’s first forays into offensive cyber operations: the regime’s 2012 attack against Saudi Aramco and 2011-2013 distributed denial of service (DDoS) attacks against U.S. financial institutions. Iranian hackers have since conducted numerous campaigns, in particular since the Trump administration came into office. (See Table 1.) In more recent campaigns, hackers have targeted dozens or hundreds of companies and individuals, not always for the same reason. For example, cybersecurity firm FireEye found that one Iranian Advance Persistent Threat (APT) group targeted aviation and energy companies in Saudi Arabia, South Korea, and the United States. FireEye hypothesized that “the targeting of the Saudi organization may have been an attempt to gain insight into regional rivals, while the targeting of South Korean companies may be due to South Korea’s recent partnerships with Iran’s petrochemical industry as well as South Korea’s relationships with Saudi petrochemical companies.”37 In contrast, the two early cases have discrete targets attacked over a limited timeframe, and therefore it is easier to extrapolate the regime’s motivations and goals as a way to understand the regime’s strategy more generally. These two cases are also well-documented in the public space by multiple sources rather than relying exclusively on the reporting of one or two private cybersecurity firms.
Table 1: Notable Examples of Iranian Cyber Operations Since January 2017
Wiper Attack on Saudi Aramco
In August 2012, the Iranian regime launched its first destructive cyberattack against a foreign adversary.d A hacker group calling itself the Cutting Sword of Justicee infiltrated the networks of Saudi Aramco and unleashed a virus dubbed Shamoon.f The malware moved quickly within the network, destroying data and rendering 35,000 computers inoperable.48 While Shamoon did not affect Aramco’s oil production, it disrupted a majority of the company’s business processes, including its supply management, shipping, and contract management.49 As this author explained in a previous study of Iranian cyber-enabled economic warfare strategy and capabilities, overnight, the Shamoon virus forced the company “to revert to faxes, inter-office mail, and typewriters. It reportedly took approximately five months to get all of the company’s systems back online.”50

That prior study also pointed out that “at the time, Iran’s oil exports were dropping rapidly as the United States increased its sanctions on Iran’s energy and financial sectors and as the EU imposed a ban on imports of Iranian crude. Thus, it is possible that Tehran hoped its cyberattacks would drive up energy prices so that Iran’s limited exports would bring in more revenue.”51 g If this were the hackers’ motivation, it would indicate that Iranian operations are more likely to target companies and industries where Tehran can reap an indirect economic benefit from the attacks.
It is also possible that Shamoon was to a small or large degree retaliation for U.S. sanctions on Iran’s energy sector. Military scholar Michael Eisenstadt concludes that “Iran has traditionally taken a tit-for-tat approach to actions by its adversaries.”52 Thus, it may be the case that targets of Iranian cyber operations are likely to mirror industries against which Washington has levied sanctions.h
Finally, Tehran may have targeted Aramco because oil is Saudi Arabia’s most important economic asset. In this case, Tehran anticipated that causing significant harm to a major source of Saudi revenue (and perhaps even undermining the global market’s faith in Saudi Arabia as a major oil producer) would weaken the Kingdom. From its founding, the Islamic Republic has conceptualized its own economy as providing the means to fortify the revolution at home and export it abroad,i and thus the regime recognizes the impact that cyber-enabled economic warfare can have. If this were Tehran’s motive, then its adversaries’ strategically significant industries will likely be among Iran’s future cyber-targets.
Operation Ababil: DDoS Attacks on U.S. Banks
Operation Ababil involved a series of DDoS campaigns against the U.S. financial sector beginning in December 2011 and continuing into mid-2013.53 The attacks occurred only intermittently for the first 10 months and then escalated to a near-weekly basis starting in September 2012, targeting 46 banks and financial institutions, according to a U.S. Department of Justice indictment.54
While DDoS attacks are relatively blunt and unsophisticated operations compared to covert infiltrations of a company’s networks, the attacks forced banks to spend tens of millions of dollars in remediation.55 One of the security researchers responsible for responding to the attack commented to The New York Times that “the scale, the scope and the effectiveness of these attacks have been unprecedented.”56 The attack primarily prevented customers from accessing mobile banking, but the fallout could have quickly spiraled had consumers begun to worry if their money was still safe in the bank. Financial institutions themselves recognized the significance of their cyber risk, and over the next two years, more than 4,000 institutions joined the Financial Sector Information Sharing and Analysis Center, an industry organization for sharing cyber threat information among financial institutions.57
In 2016, the Justice Department formally accused Tehran of sponsoring the attack, stating that the hackers were working “on behalf of the Iranian Government, including the Islamic Revolutionary Guard Corps.”58 As this campaign coincided with the last major recession Iran faced,59 U.S. officials and cybersecurity experts believe that operation was likely retaliation for U.S. economic sanctions.60 The period of time when the attacks occurred—late 2011 to early 2013—coincided with unprecedented U.S. sanctions against the Iranian financial sector, including designating the entire sector as a “jurisdiction of primary money laundering concern” under U.S. law, targeting the Iranian central bank with sanctions, and forcing the international, financial messaging system SWIFT to remove Iranian banks from its network.61 Like the Aramco attack, Operation Ababil appears to have been a cyber-enabled economic warfare campaign designed to send a message that just as the United States can impose financial sanctions on Iran, Iranian hackers can cause economic damage as well.
In both of these cases, hacker groups professing independence from the Iranian government claimed responsibility,j but the U.S. government has attributed the attacks to the Iranian government.62 This is consistent with how the regime engages with its hacker community. In Iran, there are individuals and groups of hackers who simultaneously engage in criminal activity, legitimate software development, and regime-sponsored operations.63 For example, when the U.S. Justice Department indicted Behzad Mesri for hacking and extorting HBO, the press statements and indictment itself did not indicate that this operation was at all directed by the regime in Iran.64 This same alleged hacker, however, was indicted less than 18 months later for conspiracy, espionage, and cyberattacks on behalf of the Islamic Republic.65
Cyber threat intelligence firm Recorded Future calls this a “contractor” model, in which the government and the IRGC work with trusted middlemen who “translate intelligence priorities into segmented cyber tasks.”66 Groups and individuals then vie for these contracts.67 In essence, in this system, the Iranian regime may not tell the contracted hackers precisely how and when to hit a target. Rather, the government lays out its priorities and what it wants to accomplish, and the middlemen and the hackers figure out how to best to achieve these objectives.68 In this system, hackers work on behalf of the Iranian regime when “under contract” but also freelance and work on their own projects at the same time, some of which align with regime interests and some of which are purely criminal or commercial operations.69 While there are numerous government and IRGC bodies responsible for cyber policy (including items such as censorship and infrastructure investment) and defending the regime’s own networks and there are even regime-affiliated research institutions that recruit and train would-be hackers, it appears that Iran’s offensive cyber operations are committed by individuals and groups working under government contract.70
Will Iran Retaliate for Soleimani’s Death with Cyberattacks?
The U.S. government, private sector, and allied governments therefore can anticipate that the Islamic Republic will continue to lash out in the cyber domain. Regardless of the motivation behind the attacks—whether to retaliate for the killing of Soleimani or to try to persuade Washington to relieve economic pressure from sanctions—the real-world effects may be the same: disruptive and destructive cyberattack on U.S. interests.
Indeed, prior to Soleimani’s death, the U.S. government and private cybersecurity firms were already warning of heightened Iranian cyber activity.71 Some of these warnings even predate the reported June 2019 U.S. cyberattacks on the Islamic Republic following the downing of the U.S. drone. Days prior to that U.S. operation, cybersecurity firm FireEye noted that it had already observed a widespread Iranian phishing campaign against U.S. and European governments and companies.72 According to Israeli cybersecurity firm Check Point, following Washington’s imposition of additional oil sanctions on Iran in May 2019 and through the end of the year, Iranian cyberattacks on U.S. entities doubled in comparison to the first half of 2019.73 Dragos, a cybersecurity firm specializing in industrial control systems (ICS), also observed that throughout the fall of 2019, one APT group was engaged in a broad campaign attempting to infiltrate U.S. electric utilities.74
In the weeks following the killing of Qassem Soleimani, the U.S. government issued repeated warnings to the private sector to be vigilant against Iranian cyberattacks.75 Hours after the strike, Chris Krebs, director of the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA), tweeted the same statement the Department had issued in June 2019 on Iranian cyber threats and reiterated, “time to brush up on Iranian TTPs and pay close attention to your critical systems, particularly ICS. Make sure you’re also watching third party accesses!”76
Days later, CISA issued guidance to network defenders with a series of standard cyber hygiene reminders, noting that “Iran and its proxies and sympathizers have a history of leveraging cyber and physical tactics to pursue national interests, both regionally and here in the United States.”77 DHS also issued a National Terrorism Advisory System bulletin warning that, among other threats, Iran’s cyber capabilities are sophisticated enough to cause temporary disruptions to U.S. critical infrastructure.78 While the bulletin and subsequent statement in mid-January 2020 from Acting Secretary of DHS Chad Wolf emphasized that the United States had no information indicating a specific, credible threat to the homeland,79 the FBI also issued an advisory to U.S. companies warning that Iranian hackers have increased their probing and reconnaissance activities.80
Cybersecurity firms similarly warned that companies should assume that Tehran will launch a cyberattack in response to Soleimani’s killing: John Hultquist of FireEye predicted an increase in cyber espionage against government systems in an attempt to gather intelligence and understand the United States’ likely next moves.81 His colleague Lee Foster and other analysts also warned of likely disinformation operations promoting regime propaganda.82 Robert Lee of Dragos cautioned against overreaction but urged security professionals to “proactively hunt for threats” on their networks.83 The chief information and security officer at digital risk firm Digital Shadows also urged companies to review their business continuity and recovery plans.84 And Kiersten Todt, who previously led the Commission on Enhancing National Cybersecurity, warned that Iranian hackers are likely to attempt to infiltrate the computer networks that run the physical equipment of U.S. critical infrastructure:
We should certainly expect an Iranian attempt against our infrastructure; our Industrial Control Systems are particularly vulnerable. Iranian hacking groups like APT33 (also known as Refined Kitten) [are] looking for points of ingress into the U.S. Government (Dept. of Energy, including National Labs) for disruption or espionage; [they are] also looking at how to sabotage ICS by gaining access to networks of ICS suppliers/supply chain security; [there are] reported attempts to create malware for types of ICS used in U.S. power grids and water systems.85
Credit rating agency Moody’s concluded simply that “there would likely be a wide range of potential targets.”86
Most of these warnings recognize that cyberattacks carry inherent advantages for Tehran because the regime can “cause damage without casualties.”87 Stewart Baker, former general counsel at the National Security Agency, explained that the regime is likely seeking “ways to cause pain in the United States without provoking a severe counterattack.” Dmitri Alperovitch of CrowdStrike similarly noted that the Islamic Republic perceives cyber operations as “below the thresholds likely to trigger a U.S. retaliation.”88
If Tehran decides to launch a retaliatory cyber operation, the regime will likely want to conduct an attack that does not provoke the United States to escalate, but rather keeps U.S.-Iran tensions below the threshold of traditional military confrontation. This was the conventional wisdom after the missile attack on the U.S. bases in Iraq. The attack occurred in the middle of the night, and Iran reportedly provided Iraq with advance warning.89 Coupled with President Trump’s statement and Foreign Minister Zarif’s tweet,90 it appears that the regime wanted to conduct a flashy operation while simultaneously minimizing injury, damage, and loss of life. It is worth noting, however, that this conventional wisdom may be wrong. A U.S. commander on the ground stated that Iran’s actions were intended to inflict casualties.91 And as of about a month after the missile strikes, the Pentagon has confirmed more than 100 cases of concussions and traumatic brain injury.92 This divergence of opinions on Iranian intentions may have parallels in a future cyber confrontation with Iran. If Washington misinterprets Tehran’s intentions in an attempted or successful cyberattack, it could result in either a non-response that emboldens the regime to engage in even more provocative cyberattacks or an overreaction by the United States.
Had Iran wanted to respond immediately using its cyber capabilities, it likely would have had to pre-position the capabilities. In short, most types of cyberattacks cannot happen without pre-planning: it often takes a while to scout a network to understand its vulnerabilities and develop malware that can exploit them. Only then can an actor launch a cyber operation. Indeed, Melissa Hathaway, a senior cyber advisor to Presidents Obama and George W. Bush, has stated that likely targets of Iranian operations are systems they have already “mapped.”93 And while Iranian hackers have reportedly been attempting to breach the U.S. electric grid since at least 2015,94 Tehran either did not have the right pre-positioned assets in place or could not (or chose not to) use them at this time.
While it is possible that Tehran attempted to use its pre-positioned assets but was quickly thwarted (similar to the Israeli Cyber Defense Directorate’s response in 2017), the U.S. government’s public statements indicate this was not the case. CISA Director Krebs put it this way:
“The truth here is that if the Iranians were going to do something, they would probably – it was already too late. If they were going to do something cyber – cybery – they would probably already be in a position and take the shot. We saw that they really didn’t. … [They] “didn’t have time to strategically position against energy or natural gas.”95
Taking Director Krebs’ comments at face-value, either Tehran did not have pre-positioned assets that it could deploy or the regime had assets in other sectors besides energy but decided for whatever reason not to “take the shot” at this time. Still, it is this author’s assessment that the primary concern for both the private sector and the U.S. government should be that over the medium term, Iranian hackers could increase their probing of networks in order be able to launch cyberattacks in the future at a time of the regime’s choosing.
Used exclusively as a retaliatory tool, however, a cyberattack may not provide the regime with the kind of propaganda win that it would be seeking. The U.S. State Department has concluded that “similar to the regime’s support for proxies, the Islamic Republic prioritizes plausible deniability for its malicious cyber activities.”96 In a retaliatory action, however, the regime would likely want to send a message that it can do damage to the United States and that Washington “can’t do a damn thing” to Iran, as regime leaders often boast.97 If the regime in Iran launches a cyberattack but does not claim responsibility, it loses the propaganda win. Even if the U.S. government knows the origin of the attacks, unless the regime claims credit, it cannot boast of its successes against “the Great Satan.”98 Claiming credit, however, heightens the likelihood that the United States will counter-strike at least in part to warn Iran and other cyber adversaries that there are consequences to attacks on the U.S. homeland or assets abroad.k Claiming credit also removes plausible deniability, which is one of the benefits of cyberattacks in the first place. Thus, the advantages of cyber operations and the goals of a retaliatory action are likely to run contrary, and thus of all of the types of responses Iran can conduct, a cyber operation may be the least advantageous from the regime’s perspective.l
Regardless of what the regime itself decides to do, Iranian hackers not affiliated or only loosely affiliated with the Iranian government have already begun taking the initiative to launch low-level, unsophisticated cyberattacks. Soon after the drone strike, attempted attacks against U.S. federal, state, and local government websites originating from Iranian IP addresses jumped 50 percent, according to website security firm Cloudflare.99 Pro-regime hackers successfully defaced websites belonging to the Federal Depository Library Program,100 the Texas Department of Agriculture,101 and an Alabama veterans organization.102 This type of defacement is very simplistic and therefore likely conducted by pro-regime hacktivists looking for the least secure .gov and other websites to score propaganda victories rather than hackers contracted by the Iranian government to conduct a meaningful cyber operation to damage the United States and its allies.
In the days following Soleimani’s death, pro-regime, pro-Soleimani, and anti-American messages also exploded on Twitter.103 Broadly speaking, in recent years, the Islamic Republic has expanded its influence and disinformation operations from traditional state-owned media outlets to social media as well.104 Researchers assessed that the latest campaign was likely a coordinated effort given how rapidly the hashtag #HardRevenge spread and the fact that the accounts amplified the same messages and were all created within the past few months.105 It is not clear, however, if the regime was behind the coordination or if merely regime-aligned activists were involved.
There is likely to be a proliferation of attacks aligned with the regime’s interests but not necessarily directed by Tehran because of the “contractor” nature of the Iranian hacker community, as discussed earlier. Iranian hackers of varying skill levels may take the initiative to launch attacks they believe the regime would want them to undertake, even when they do not receive direct orders or requests from the government to launch these operations. And because hackers vie for government contracts awarded by middlemen, amateurs may have an incentive to engage in flashy cyber operations at least in part as a way to gain the attention of the middlemen who can award them contracts in the future.
All hackers—ranging from both more professional groups that have conducted government operations in the past to amateur hacktivists—are likely to continue and indeed proliferate their cyber operations. It is difficult to predict, however, if the regime itself will respond to Soleimani’s death by commissioning new cyber operations. And yet, it is safe to assume based on past activities that the regime will continue to launch cyber operations as a response to U.S. economic sanctions and other pressure. In short, cyberattacks by Iranians are likely to escalate because hackers believe they are doing what the regime wants them to do, even though they may not receive direct instructions. Meanwhile, the Iranian regime is likely to continue to commission cyberattacks as a response to U.S. economic pressure. These two factors indicate that the Iranian cyber threat will not decrease following Soleimani’s death and may in fact increase because of the operations of independent hackers. But, at the same time, the regime may not issue new contracts for cyber operatives to take new actions as a retaliation for Soleimani’s death, and thus, his death may also not cause a step-change in the cyber threat that the Iranian regime itself poses. From a U.S. intelligence perspective, these distinctions are important. However, for the victims of Iranian cyber operations, whether the motivation is retaliation for Soleimani’s death or a reaction to U.S. sanctions matters little. The real-world effects are similar.
Tehran is likely to focus these cyberattacks on the U.S. private sector rather than direct attacks on the more fortified U.S. government systems for a couple of reasons: 1) The private sector is a ‘soft’ target, which tends to be what the hackers working on behalf of the regime hit;106 and 2) there have been no publicly reported instances of the U.S. military responding to a cyberattack on private industry with traditional military strikes. (These attacks can do damage with a low risk of provoking a military counter-response.) Examining past Iranian attacks offers some indication of the specific industries that Iranian hackers will attempt to target. Iranian hackers are likely to hit sectors of the U.S. industry 1) that mirror those Iranian economic sectors targeted under U.S. sanctions and/or 2) that Tehran deems strategically significant to the U.S. economy and national power.
Washington’s ability to wield financial power in the form of sanctions is largely the result of the size of the U.S. economy and the dominant role of the dollar in global trade.107 Targeting the U.S. financial sector (similar to Operation Ababil but perhaps using very different attack vectors) would thus both attack the power Washington uses to apply sanctions on Iran as well as mirror the fact Washington has sanctioned the Iranian financial sector.108 Commercial banks have hardened their systems since 2013, but hackers could still hit the U.S. financial system by targeting companies that facilitate transactions, payments, and trading, as explained recently by financial fraud and data breach analyst Al Pascual.109 “I would imagine that U.S. organizations that are critical to facilitating financial transactions, like consumer or commercial payments and trading activity, will be at the top of Iran’s hit list,” he said.110
These attacks could be significant. CISA Director Chris Krebs has warned that “Iran has the capability and the tendency to launch destructive attacks.”111 The U.S. intelligence community’s annual Worldwide Threat Assessment noted that Tehran is “capable of causing localized, temporary disruptive effects,”112 and as noted earlier, the Dragos report warned that an APT group has been attempting to infiltrate the U.S. electric grid.113 Microsoft’s security experts observed similar activities and speculated that if successful, Iranian hackers might use their ICS access to launch attacks with disruptive or destructive effects in the physical world.114
While Iranian hackers cannot affect the entire grid system, they could disrupt electricity at a local level.115 And if the Islamic Republic believes that the U.S. government will not respond militarily, the regime may be more likely to unleash its hackers to conduct a risky operation like temporarily disrupting the electric grid in a localized area either to try to coerce the U.S. government into relieving economic pressure, to demonstrate the sophistication of its cyber capabilities, to simply embarrass the United States, or to achieve other regime objectives.
Finally, Iranian hackers could also use their demonstrated capabilities in new ways. For example, Iranian hackers were responsible for the SamSam ransomware attacks on major U.S. cities and healthcare-related companies.116 SamSam disrupted municipal functions but primarily from a billing and paperwork perspective. Could similar attacks instead be directed in such a way to affect not utility bills but the utilities themselves, particularly the delivery of lifeline services like water and sewage?
The situation could quickly escalate due to Iranian miscalculation or purposeful risky behavior. Suzanne Spaulding, former chief cyber official at DHS during the Obama administration, noted that the regime has “a high tolerance for escalating risk,” pointing in particular to the 2011 plot to assassinate the Saudi ambassador to the United States at a popular Washington, D.C., restaurant.117 The “current risk of escalatory action by Iran is particularly high, given that the ‘red lines’ are not clearly defined in cyberspace,” she explained.118
Conclusion
While the United States has yet to suffer a debilitating cyberattack at the hands of the Islamic Republic, the threat has not diminished, and continued vigilance by the U.S. government and private sector is critical. Whether as a retaliatory strike for the killing of Qassem Soleimani or as part of its campaign to pressure the United States to lift economic sanctions, Tehran is likely plotting its next move in cyberspace.
In fact, Soleimani’s death may have little impact on the cyber threat posed by the Iranian government. Based on statements from Iranian government officials119 as well as the structure of Iran’s military forces and trend lines of its recent operations,120 the killing of Soleimani is unlikely to have reduced the regime’s appetite for dangerous and aggressive behavior, and thus Tehran is likely to continue its malign activity in cyberspace. As discussed, regime-sponsored attacks were already ongoing prior to the January 2020 drone strike and have continued since at least in part because of the damage that U.S. sanctions are imposing on Iran. And while hackers appear to be taking their own initiative to launch cyber operations in retaliation for the killing of Soleimani, based on public information, there is no evidence at this point that the regime itself has issued new directions to middlemen to contract out new cyber operations to retaliate for the U.S. killing of General Soleimani.
Over the longer term, it will be important to assess how much control the regime has over its contractors, specifically related to the question of whether and what might happen if contractors engage in riskier and more destructive attacks than the regime wants. Might this situation force the regime to exert greater control over its hacker community? And how would this change the U.S. intelligence community’s assessment of the Iranian cyber threat? At the same time, however, the contractor model and plausible deniability may enable or encourage the regime to take greater risks in the future—something which must also be factored into U.S. threat assessments.
For now, however, even as the Defense Department has announced a new cyber strategy focused on engaging the adversary in cyberspace outside of U.S. government networks and potentially on the adversary’s own networks to “to disrupt or halt malicious cyber activity at its source”121– a policy known as “defend forward”m – the U.S. government more broadly has continued to rely on law enforcement and financial sanctions tools to combat malicious cyber activities.122 Yet these actions seem to have failed to deter Iranian hackers. For example, after the Department of Justice indicted nine state-sponsored Iranian hackers engaged in a massive cyber theft operation against universities in the United States and around the world,123 the same hackers resumed their activities only months later.124 The indictment has no real-world impact because the U.S. government simply cannot extradite these hackers, and the Iranian government appears not to have rescinded their ‘contract’ as a result of them getting caught.
Thus, rather than focusing on deterrence through punishment (particularly if the punishment is confined to actions that amount to naming and shaming hackers), the United States may be more successful at preventing or at a minimum thwarting Iranian cyber operations by focusing on deterrence through denial—that is, by preventing the Islamic Republic from achieving its desired outcomes in cyberspace. Regardless of the regime’s motives, the United States is more likely to be able to prevent attacks by ensuring the targets of Iranian malicious cyber operations have the specific information they need to defend themselves or remediate and recover quickly in the event of an attack. For example, in the days following Soleimani’s death, the New York Department of Financial Services (DFS) not only provided general cyber hygiene recommendations to all regulated entities, but also warned these companies that “Iranian hackers are known to prefer attacking over the weekends and at night precisely because they know that weekday staff may not be available to respond immediately.” DFS then reminded these companies to ensure that their alert systems respond quickly “even outside of regular business hours.”125
While examining prior Iranian cyber operations provides insights into possible future targets, to be best prepared to thwart Iranian cyber operations, it is necessary to understand what Tehran views as the industries that are critical to U.S. power. This type of assessment, paired with the analysis of regular chatter on hacker forums and other intelligence, may illuminate a list of possible future targets of Iranian cyber operations. These future targets would thus be the priority list for U.S. government engagement with the private sector on cyber defense. If the partnership between government and industry can reduce the effects of the Islamic Republic’s cyber operations, the United States will have weakened a key pillar of Tehran’s asymmetric strategy. CTC
Annie Fixler is the deputy director of the Center on Cyber and Technology Innovation at the Foundation for Defense of Democracies, a Washington-based, nonpartisan research institute focusing on national security and foreign policy. Follow @afixler
Substantive Notes
[a] When conducting a phishing attack, hackers send fraudulent emails impersonating another individual or company to convince the recipient to click on a malicious link, download a piece of malware, or enter credentials on fake websites.
[b] While Houthi militants in Yemen have claimed responsibility, the Trump administration has dismissed these statements and blamed the Islamic Republic of Iran. The public evidence supports the administration’s assertion but is not definitive. David D. Kirkpatrick, Christoph Koettl, Allison McCann, Eric Schmitt, Anjali Singhvi, and Gus Wezerek, “Who Was Behind the Saudi Oil Attack? What the Evidence Shows,” New York Times, September 16, 2019; “Special Report: ‘Time to take out our swords’ – Inside Iran’s plot to attack Saudi Arabia,” Reuters, November 25, 2019; Erin Cunningham, “Iran’s gamble: Analysts say brazen attack aimed to pressure U.S. with little fear of reprisal,” Washington Post, September 20, 2019.
[c] There is also some evidence suggesting that Iranian hackers may also be more likely than their counterparts to launch operations where they cannot predict the precise real-world effects or the victim’s response. For example, an Iranian hacker affiliated with the IRGC infiltrated the Bowman Dam in Rye, New York, between August 28 and September 18, 2013. It is unclear why a hacker would target this 20-foot dam. It is possible that the hack was a dry run for a more spectacular operation or that the hacker got the dam mixed up with a much larger facility with the same name. If the latter, and if analysts are correct that the hacker intended to take over the dam’s functions, did this hacker and the Iranian government understand the full implication of causing a physically destructive cyberattack against U.S. critical infrastructure? “Seven Iranians Working for Islamic Revolutionary Guard Corps-Affiliated Entities Charged for Conducting Coordinated Campaign of Cyber Attacks Against U.S. Financial Sector,” U.S. Department of Justice, March 24, 2016; Joseph Berger, “A Dam, Small and Unsung, Is Caught Up in an Iranian Hacking Case,” New York Times, March 25, 2016.
[d] The Islamic Republic of Iran has continued to deny its responsibility for this attack, but it is commonly accepted that this was a state-backed operation.
[e] The Iranian hacker group Cutting Sword of Justice claimed responsibility for the Aramco hack on this message board: Statement, “Untitled,” Pastebin, Cutting Sword of Justice, August 15, 2012.
[f] The virus also appears to have struck Qatari natural gas producer RasGas, although much less is known publicly about this case including the overall damage inflicted. Much of the public reporting at the time linked RasGas and Aramco but did not provide evidence (technical data, company statements, or other documentation) beyond the coincidence of timing and roughly similar outages at both companies to support this assertion. See, for example, Camilla Hall and Javier Blas, “Qatar group falls victim to virus attack,” Financial Times, August 30, 2012, and Kim Zetter, “Qatari Gas Company Hit With Virus in Wave of Attacks on Energy Companies,” Wired, August 30, 2012.
[g] If this were indeed the hackers’ motivations, they failed to achieve their objectives. While global prices were elevated at the time, they did not spike after the attacks. “2012 Brief: Average 2012 crude oil prices remain near 2011 levels,” U.S. Energy Information Administration, January 10, 2013.
[h] Some analysts also believe that Shamoon was retaliation for a cyberattack on Iran’s own energy sector. Author interview, cybersecurity analyst, October 2018; “Suspected cyber attack hits Iran oil industry,” Reuters, April 23, 2012.
[i] The Iranian constitution states that the economy “is a means that is not expected to do anything except better facilitate reaching the goal [of advancing the Islamic revolution].” Constitution of the Islamic Republic of Iran 1979 (as last amended on July 28, 1989), Preamble.
[j] The Iranian hacker group Cutting Sword of Justice claimed responsibility for the Aramco hack on this message board: Statement, “Untitled,” Pastebin, Cutting Sword of Justice, August 15, 2012. See also Thomas Brewster, “U.S. Accuses 7 Iranians Of Cyberattacks On Banks And Dam,” Forbes, March 24, 2016. The hacker group Izz ad-Din al-Qassam claimed responsibility for the DDoS attacks. See Rym Momtaz and Lee Ferran, “US Bank Cyber Attackers Deny Iran Connection,” ABC News, November 12, 2012.
[k] Iranian state-backed hackers have conducted numerous cyberattacks on U.S. interests around the world, including attacks on U.S. allies. Based on public information, none of these has prompted a U.S. military response. If, however, the Iranian regime is responsible for a direct cyber attack on the U.S. homeland or U.S. troops, embassies, or other assets—not U.S. allies or interests, but on Americans—Washington is much more likely to respond with force. This distinction may also explain why the drone and missile attacks on Saudi Arabia did not prompt a U.S. military response but the death of a U.S. contractor and the subsequent attacks on the U.S. embassy in Baghdad prompted military strikes, including the drone strike that killed Soleimani.
[l] Jan Kallberg, a research scientist at the Army Cyber Institute at West Point and assistant professor at the U.S. Military Academy, has argued that a counter cyber strike on Iran is particularly dangerous for the Islamic Republic because of the instability and internal opposition to the government. Jan Kallberg, “Why Iran would avoid a major cyberwar,” Fifth Domain, January 17, 2020. For additional analysis on why Tehran may not find cyberattacks an attractive retaliatory measure, see Jackie Schneider, “Iran can use cyberattacks against the U.S. That’s not nearly as bad as it sounds,” Washington Post, January 6, 2020.
[m] As Robert Chesney, associate dean at the University of Texas Law School, explains, “defense forward entails operations that are intended to have a disruptive or even destructive effect on an external network: either the adversary’s own system or, more likely, a midpoint system in a third country that the adversary has employed or is planning to employ for a hostile action.” Robert Chesney, “The 2018 DOD Cyber Strategy: Understanding ‘Defense Forward’ in Light of the NDAA and PPD-20 Changes,” Lawfare, September 25, 2018.
Citations
[1] Behnam Ben Taleblu, “Making sense of Iranian escalation,” FDD’s Long War Journal, May 20, 2019.
[2] “Remarks by President Trump on the Joint Comprehensive Plan of Action,” White House, May 8, 2018; Michael R. Pompeo and Steven T. Mnuchin, “Update on Iran Policy and Sanctions,” briefing at the Foreign Press Center, November 5, 2018.
[10] Raphael Satter and Christopher Bing, “Exclusive: Iran-linked hackers pose as journalists in email scam,” Reuters, February 5, 2020; “Fake Interview: The New Activity of Charming Kitten,” Certfa Lab, February 5, 2020.
[11] Julian E. Barnes and Thomas Gibbons-Neff, “U.S. Carried Out Cyberattacks on Iran,” New York Times, June 22, 2019; Ellen Nakashima and Paul Sonne, “U.S. military carried out secret cyberstrike on Iran to prevent it from interfering with shipping,” Washington Post, August 28, 2019.
[14] “Treasury Designates Individual, Entity Posing Threat to Stability in Iraq,” U.S. Department of the Treasury, July 2, 2009; “The Foreign Terrorist Organization List,” Congressional Research Service, updated January 15, 2019.
[22] Tim Starks, “FBI stresses vigilance against pro-Iranian hackers,” Politico, January 30, 2020.
[24] Rebecca Klar, “Soleimani successor vows revenge for US strike,” Hill, January 6, 2020; “Soleimani successor: continuity figure in uncertain times,” Agence France-Presse, January 8, 2020.
[25] Sam Jones, “Cyber warfare: Iran opens a new front,” Financial Times, April 26, 2016.
[26] Ibid.
[28] Annie Fixler and Frank Cilluffo, Evolving Menace: Iran’s Use of Cyber-Enabled Economic Warfare (Washington, D.C.: Foundation for Defense of Democracies, 2018). For an in depth look at the Islamic Republic of Iran’s concepts and doctrines of warfare, see J. Matthew McInnis, Iranian Concepts of Warfare: Understanding Tehran’s Evolving Military Doctrines (Washington, D.C.: American Enterprise Institute, February 2017).
[30] Iran Action Group, Outlaw Regime: A Chronicle Of Iran’s Destructive Activities (Washington, D.C.: U.S. Department of State, 2018), p. 32.
[31] Collin Anderson and Karim Sadjadpour, Iran’s Cyber Threat: Espionage, Sabotage, and Revenge (Washington, D.C.: Carnegie Endowment for International Peace, 2018), p. 6.
[32] Fixler and Cilluffo.
[33] “Leafminer: New Espionage Campaigns Targeting Middle Eastern Regions,” Symantec, July 25, 2018; “Rocket Kitten: A Campaign with 9 Lives,” Check Point, 2015; Robert Falcone and Bryan Lee, “The OilRig Campaign: Attacks on Saudi Arabian Organizations Deliver Helminth Backdoor,” Palo Alto Networks, May 26, 2016.
[34] Anderson and Sadjadpour, pp. 34-35; “The Iranian-Saudi Conflict and Its Cyber Outlet,” Recorded Future, June 26, 2015.
[35] Yoav Limor, “Cyber Defense Head: Iranians Attempt to Disrupt Home Front Command,” Israel Hayom, February 8, 2018; Gwen Ackerman, “Iranian Hackers Drew Worryingly Close to Israel’s Missile Alarm,” Bloomberg, February 24, 2019.
[36] Ms. Smith, “Saudi Arabia again hit with disk-wiping malware Shamoon 2,” CSO, January 24, 2017; “Shamoon 2 Malware,” IBM X-Force Exchange, accessed February 5, 2020; “Shamoon: Multi-staged destructive attacks limited to specific targets,” Symantec, January 27, 2017.
[38] Muks Hirani, Sarah Jones, and Ben Read, “Global DNS Hijacking Campaign: DNS Record Manipulation at Scale” FireEye, January 9, 2019. The FireEye report coincided with a DHS emergency directive about DNS spoofing, although it is unclear if these were the same or different campaigns. “Mitigate DNS Infrastructure Tampering,” Emergency Directive 19-01, U.S. Department of Homeland Security, January 22, 2019.
[39] Ackerman.
[40] “Leafminer: New Espionage Campaigns Targeting Middle Eastern Regions.”
[44] Tom Burt, “Recent cyberattacks require us all to be vigilant,” Microsoft, October 4, 2019.
[45] Andy Greenberg, “Iranian Hackers Have Been ‘Password-Spraying’ the US Grid,” Wired, January 9, 2020; North American Electric Cyber Threat Perspective (Hanover, MD: Dragos, 2020), pp. 1, 4, 6, and 10.
[48] Jose Pagliery, “The inside story of the biggest hack in history,” CNN Money, August 5, 2015; Nicole Perlroth, “In Cyberattack on Saudi Firm, U.S. Sees Iran Firing Back,” New York Times, October 23, 2012.
[49] Pagliery.
[50] Fixler and Cilluffo.
[51] Ibid.
[54] “Seven Iranians Working for Islamic Revolutionary Guard Corps-Affiliated Entities Charged for Conducting Coordinated Campaign of Cyber Attacks Against U.S. Financial Sector,” U.S. Department of Justice, March 24, 2016; Indictment, United States of America v. Ahmad Fathi et al, 16 Cr. (S.D.N.Y filed March 16, 2016).
[55] “Seven Iranians Working for Islamic Revolutionary Guard Corps-Affiliated Entities Charged.”
[56] Perlroth and Hardy.
[57] Cyber-enabled economic warfare tabletop exercise, not-for-attribution remarks, hosted by the Foundation for Defense of Democracies, Washington, D.C., October 2018.
[58] Indictment, United States of America v. Ahmad Fathi et al.
[59] Mark Dubowitz and Rachel Ziemba, “When Will Iran Run Out of Money?” Foundation for Defense of Democracies and Roubini Global Economics, October 1, 2013; Mark Dubowitz, Jennifer Hsieh, and Rachel Ziemba, “Iran’s Economy Will Slow But Continue To Grow Under Cheaper Oil and Current Sanctions,” Foundation for Defense of Democracies and Roubini Global Economics, February 4, 2015.
[60] Perlroth and Hardy. See also Fixler and Cilluffo.
[62] “Seven Iranians Working for Islamic Revolutionary Guard Corps-Affiliated Entities Charged;” Dante D’Orazio, “US officials claim Iran behind cyberattack on Saudi oil firm, suggest it’s a retaliation,” Verge, October 24, 2012.
[63] Anderson and Sadjadpour, pp. 18, 23-25.
[66] Levi Gundert, Sanil Chohan, and Greg Lesnewich, Iran’s Hacker Hierarchy Exposed: How the Islamic Republic of Iran Uses Contractors and Universities to Conduct Cyber Operations (Somerville, MA: Recorded Future, 2018).
[67] For more information on how and why this system developed, see Fixler and Cilluffo.
[68] For comparison, Russia tends to “piggy back” on criminal hackers when conducting its operations while China relies on hackers employed directly by the government. Boris Zilberman, Kaspersky and Beyond Understanding Russia’s Approach to Cyber-Enabled Economic Warfare (Washington, D.C.: Foundation for Defense of Democracies, 2018), pp. 13-15; Zack Cooper, Understanding the Chinese Communist Party’s Approach to Cyber-Enabled Economic Warfare (Washington, D.C.: Foundation for Defense of Democracies, 2018), pp. 13-16.
[69] For additional analysis of the Iranian regime’s relationship with hackers and its historical reliance on proxies, see Tim Maurer, Cyber Mercenaries: The State, Hackers, and Power (New York: Cambridge University Press: 2018), Chapter 5, “Cyber Proxies on a Loose Leash: Iran and Syria.”
[70] See section on “Architecture of Cyber Warfare” in Fixler and Cilluffo.
[72] Greenberg, “Iranian Hackers Launch a New US-Targeted Campaign as Tensions Mount.”
[73] Mazzetti, Bergman, and Fassihi.
[75] For example, U.S. Department of Homeland Security, “Increased Geopolitical Tensions and Threats,” CISA Insights, January 6, 2020.
[77] “Increased Geopolitical Tensions and Threats.”
[82] Eduard Kovacs, “Iran May Respond With Cyberattacks to Killing of Qassem Soleimani,” Security Week, January 3, 2020; Tony Romm, Isaac Stanley-Becker, and Craig Timberg, “‘A cyberattack should be expected’: U.S. strike on Iranian leader sparks fears of major digital disruption,” Washington Post, January 3, 2020.
[83] Lyngaas and Vavra.
[84] Kovacs.
[86] Michael B. Farrell, “Signs of hacking in Georgia prior to 2016 vote,” Politico, January 17, 2020.
[87] Marks.
[88] Ibid.
[89] Martin Chulov, “Dialled down: Iran’s phoned-in attack just enough to ease tensions,” Guardian, January 8, 2020; Howard Altman, Aaron Mehta, Shawn Snow, and Meghann Myers, “Iran didn’t kill anyone in missile attack, spurring hopes for de-escalation,” Military Times, January 8, 2020.
[90] Leary, Youssef, Eqbali, and Rasmussen; Zarif.
[96] Outlaw Regime, p. 31.
[97] “US embassy attack: Trump threatens Iran over violent protest in Iraq,” BBC, January 1, 2020.
[104] Patrick Tucker, “Iran Is Expanding Its Online Disinformation Operations,” Defense One, January 9, 2020. See also Adam Rawnsley, “New York Post Reporter’s Identity Hijacked to Spread Pro-Iran Propaganda,” Daily Beast, January 8, 2020.
[105] Stone.
[106] Outlaw Regime, p. 31.
[107] Juan Zarate, Testimony, “Sanctions and Financial Pressure: Major National Security Tools,” House Foreign Affairs Committee, January 10, 2018, p. 5; Eric B. Lorber, Securing American Interests: A New Era of Economic Power (Washington, D.C.: Foundation for Defense of Democracies, 2017), p. 11. For an in-depth analysis of U.S. economic power and the use of sanctions, see Juan Zarate, Treasury’s War: The Unleashing of a New Era of Financial Warfare (New York: PublicAffairs, 2013).
[108] See, for example, David Cohen, Testimony, “Negotiations on Iran’s Nuclear Program,” Senate Committee on Foreign Relations, February 4, 2014; and Dubowitz and Fixler, pp. 8-16.
[109] Penny Crosman, “Should banks expect cyberattacks from Iran?” American Banker, January 7, 2020.
[110] Ibid.
[112] Coats, p. 6.
[113] North American Electric Cyber Threat Perspective, pp. 1, 4, 6, and 10.
[115] Marks.
[117] Kovacs.
[118] Ibid.
[119] Klar; “Soleimani successor: continuity figure in uncertain times.”
[120] Behnam Ben Taleblu, “Remember, Iran’s Terror Network Is Global,” Radio Farda, February 8, 2020; Behnam Ben Taleblu, “Iran is increasingly using missiles in its military operations — that’s a problem,” Hill, January 21, 2020.
[121] “Summary of Department of Defense Cyber Strategy,” U.S. Department of Defense, September 2018.
[124] Charlie Osborne, “Iranian hackers target 70 universities worldwide to steal research,” ZDNet, August 24, 2018; Danny Palmer, “Iranian hackers resume credential-stealing phishing attacks against universities around the world,” ZDNet, September 11, 2019; Sean Lyngaas, “‘Cobalt Dickens’ group is phishing universities at scale again, researchers say,” CyberScoop, September 11, 2019.
 Skip to content
Skip to content

